环境及工具
windows 7 32 企业版
Peach Fuzzer
WinDbg
SocketSniff
Easy File Sharing Web Server 6.8
实践
安装完就可以打开页面,开启SocketSniff进行监听,跟着以guest模式登录
跟着我们就可以捕捉到请求(其实这个用wireshark也是可以的啦)
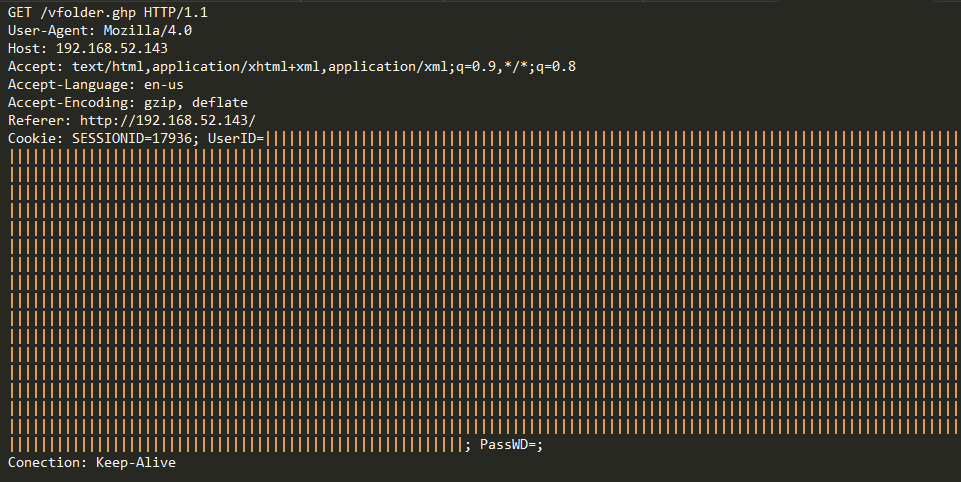
1 | GET /vfolder.ghp HTTP/1.1 |
我们跟着作者fuzz最后一行——Cookie吧
接下来我们根据上面的请求编写Peach Pit,就是一个描述性的xml文件
1 | <?xml version="1.0" encoding="utf-8"?> |
之后输入命令就可以开始fuzz了(TestVfolder是跟Test的name一致)
1 | Peach.exe -DHOST=192.168.52.143 -DPORT=80 ./remotefuzz/efs_fuzz.xml TestVfolder |
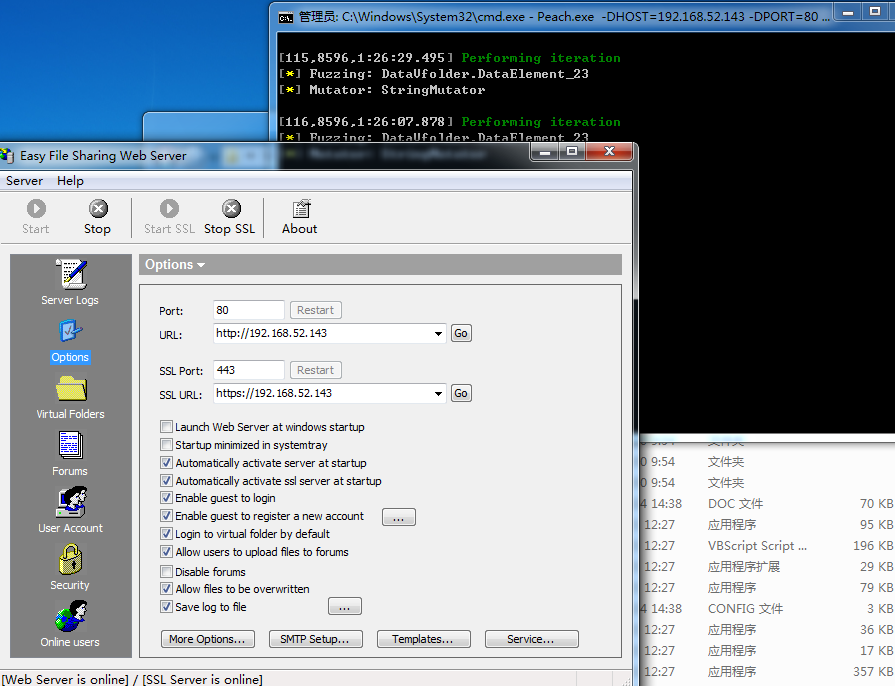
这软件垃圾,过不了几秒就蹦几个了
打开原始payload看看,一看就知道是缓冲区溢出了
reference
https://blog.techorganic.com/2014/05/14/from-fuzzing-to-0-day/


