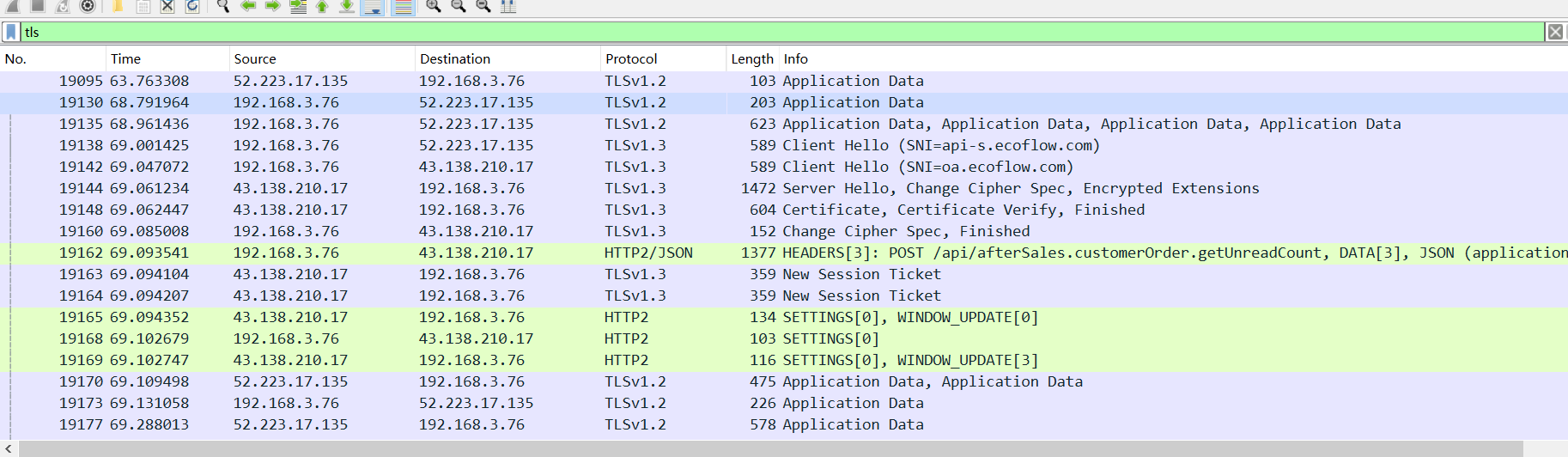
使用的方案:https://github.com/lasting-yang/frida_bypass_ssl_example
下载tcpdump
https://www.androidtcpdump.com/android-tcpdump/downloads64bit
1 | adb push .\tcpdump /data/local/tmp |
手机运行frida-server
1 | OnePlus3:/data/local/tmp # ./frida-server-16.2.1-android-arm64 |
运行获取sslkey_log
1 | python sslkey_log.py packagename |
之后再安卓上开启抓包
1 | data/local/tmp/tcpdump -i any -U -w test.pcap |
拿到电脑上wireshark打开
1 | adb pull /data/local/tmp/test.pcap test.pcap |
配置首选项
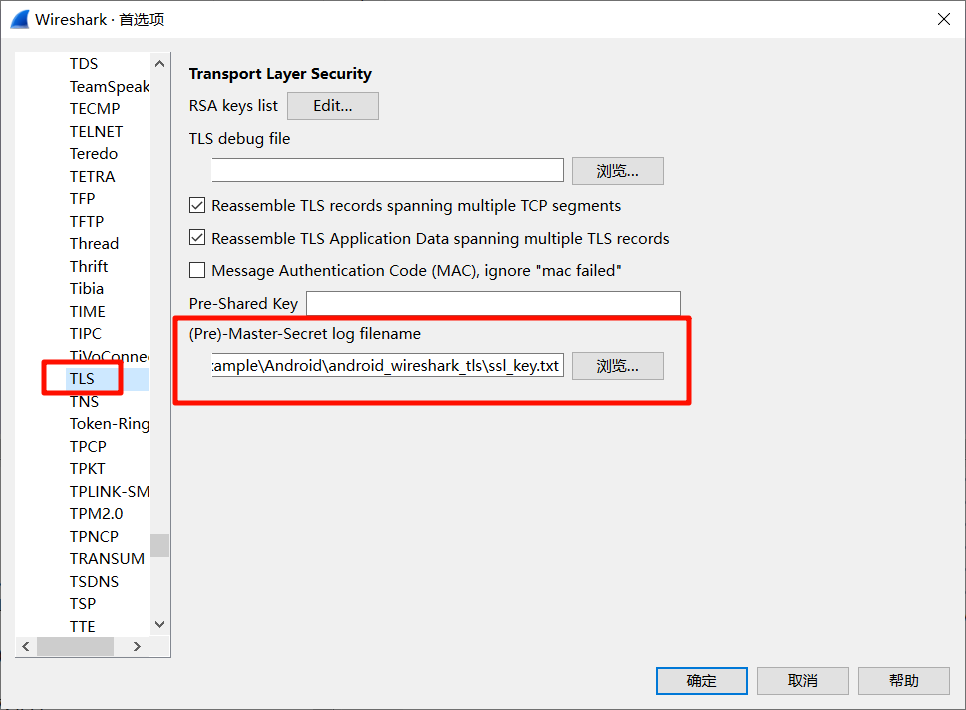
tls进行过滤,就可以到解密的http的包了